HashiCorp Vault’s Zero-Day Nightmare: Nine Flaws That Shatter Its Trust Model
Introduction
Hello everyone — if you were banking on HashiCorp Vault being your impenetrable treasure chest of secrets, here’s your wake-up call: the Cyata research team just found nine zero-day vulnerabilities in it, and they’re not the sort you can shrug off. These aren’t minor cracks; they’re structural faults that can lead straight to impersonation, privilege escalation, MFA bypass and even full-on remote code execution. In vault terms, that means the robbers aren’t just in the lobby — they own the building.
What Is It? Who Is It For?
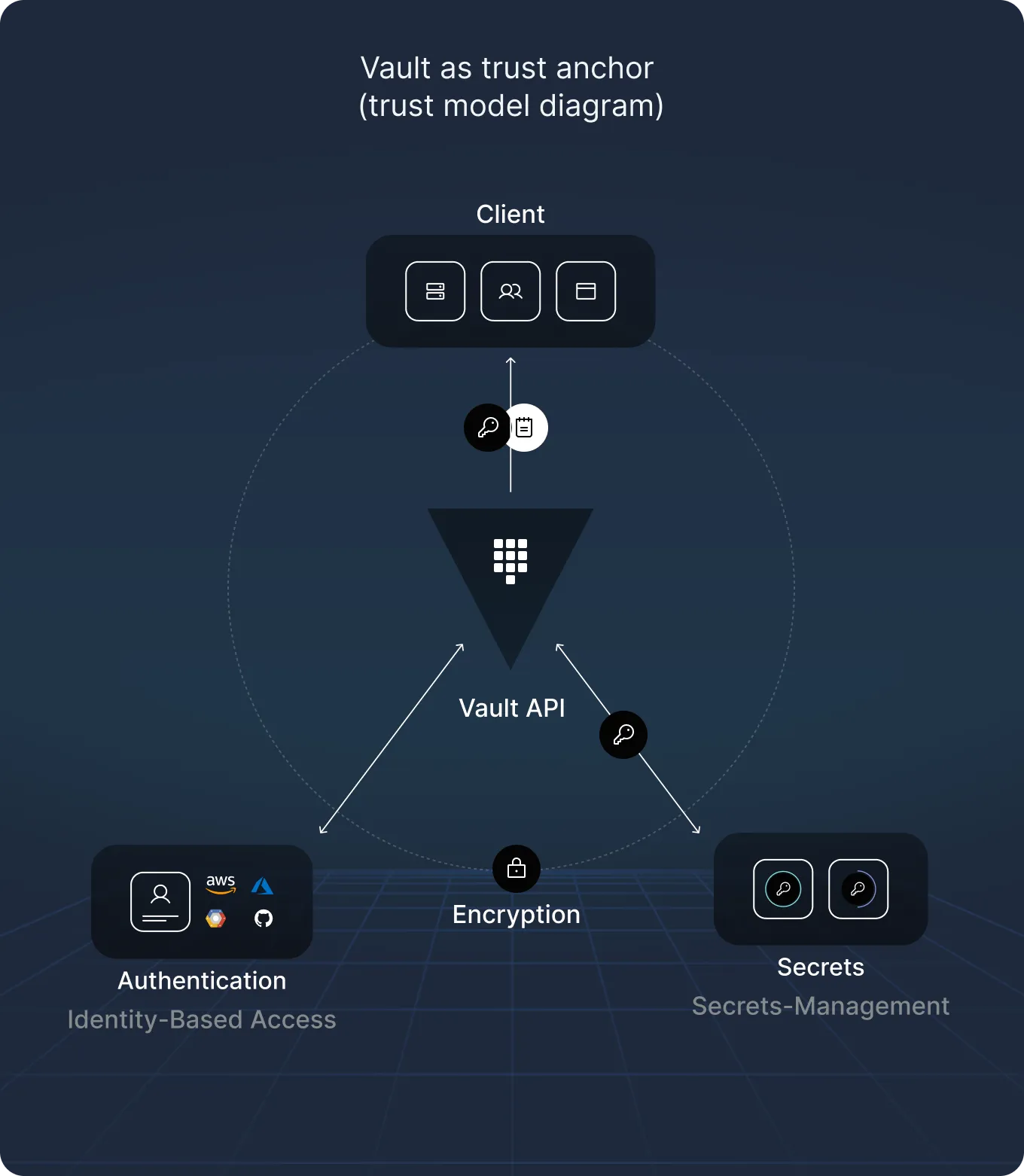
HashiCorp Vault is an open-source secrets management system used by everyone from startups to big-league enterprises. Its job is to store and broker access to sensitive assets — API keys, credentials, certificates, encryption keys — all managed through fine-grained identity-based policies. It sits at the heart of DevSecOps pipelines, acting as the final gatekeeper before anyone or anything touches your most protected data. Breach Vault, and you’ve essentially breached the whole kingdom.
Design and Experience
On the surface, Vault looks like a security engineer’s dream: API-friendly, flexible integrations, and rigorous policy controls. Under the hood, however, Cyata’s deep manual source code review uncovered that some of Vault’s most critical enforcement logic — in authentication, identity resolution, and policy checks — has been quietly betraying administrators for as long as a decade. These aren’t obvious usability faults; they are hidden misalignments between how Vault thinks it enforces trust and what it actually does when a maliciously crafted request comes knocking.
Quality, Performance, and Reliability
Performance-wise, there’s no indication Vault was sluggish or crashing. The issues here are more insidious: logic flaws that work consistently, silently, and without error messages that might tip off defenders. You get the speed, you get the stability — you just also get exploitable behavior baked into the authentication workflow, authorization routines, and plugin system. In medical terms, Vault looked healthy in triage but the X-rays showed the arteries were 90% blocked.
Features and Capabilities
- Secrets Management: API-accessible, central storage for secrets, dynamic credential provisioning, encryption services, certificate management.
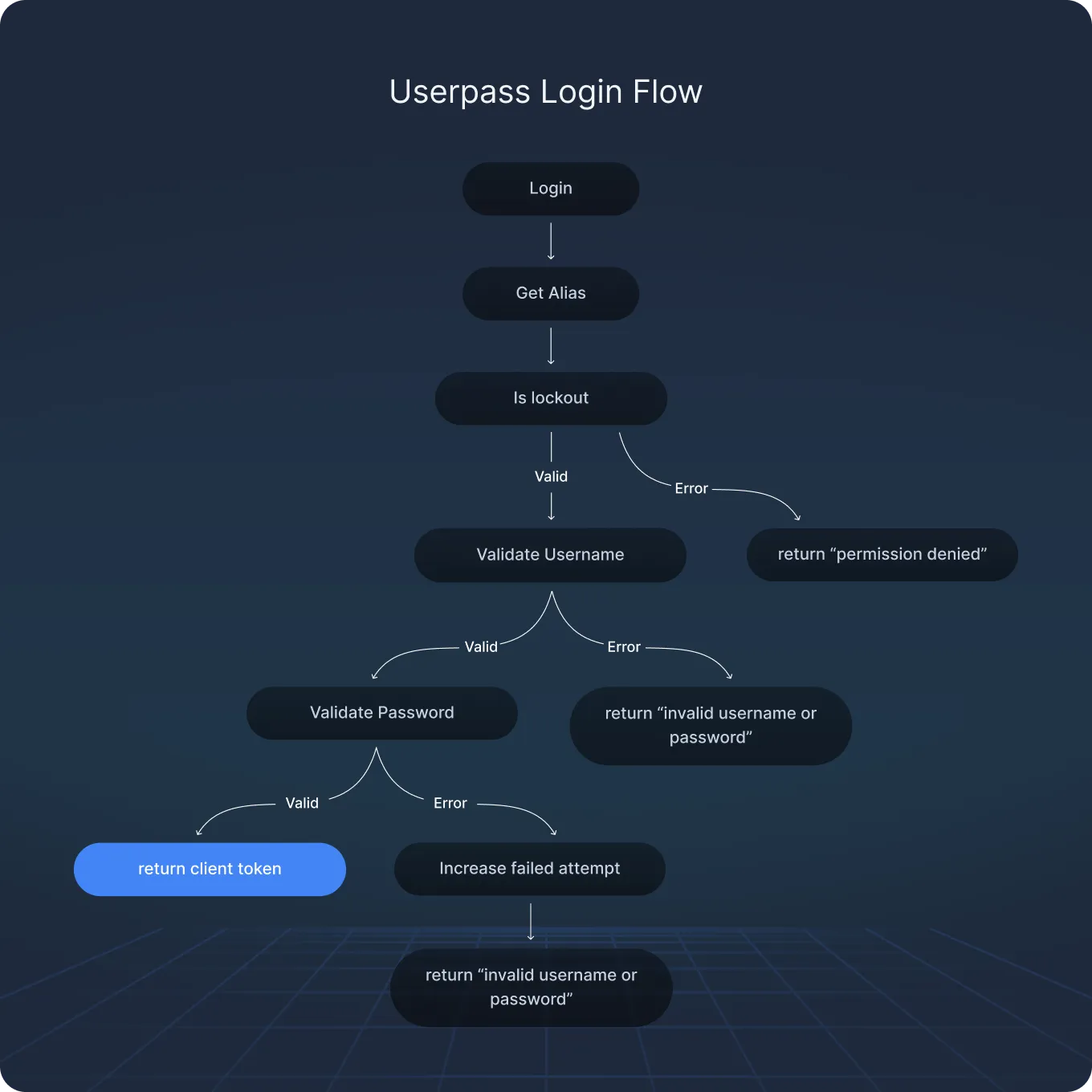
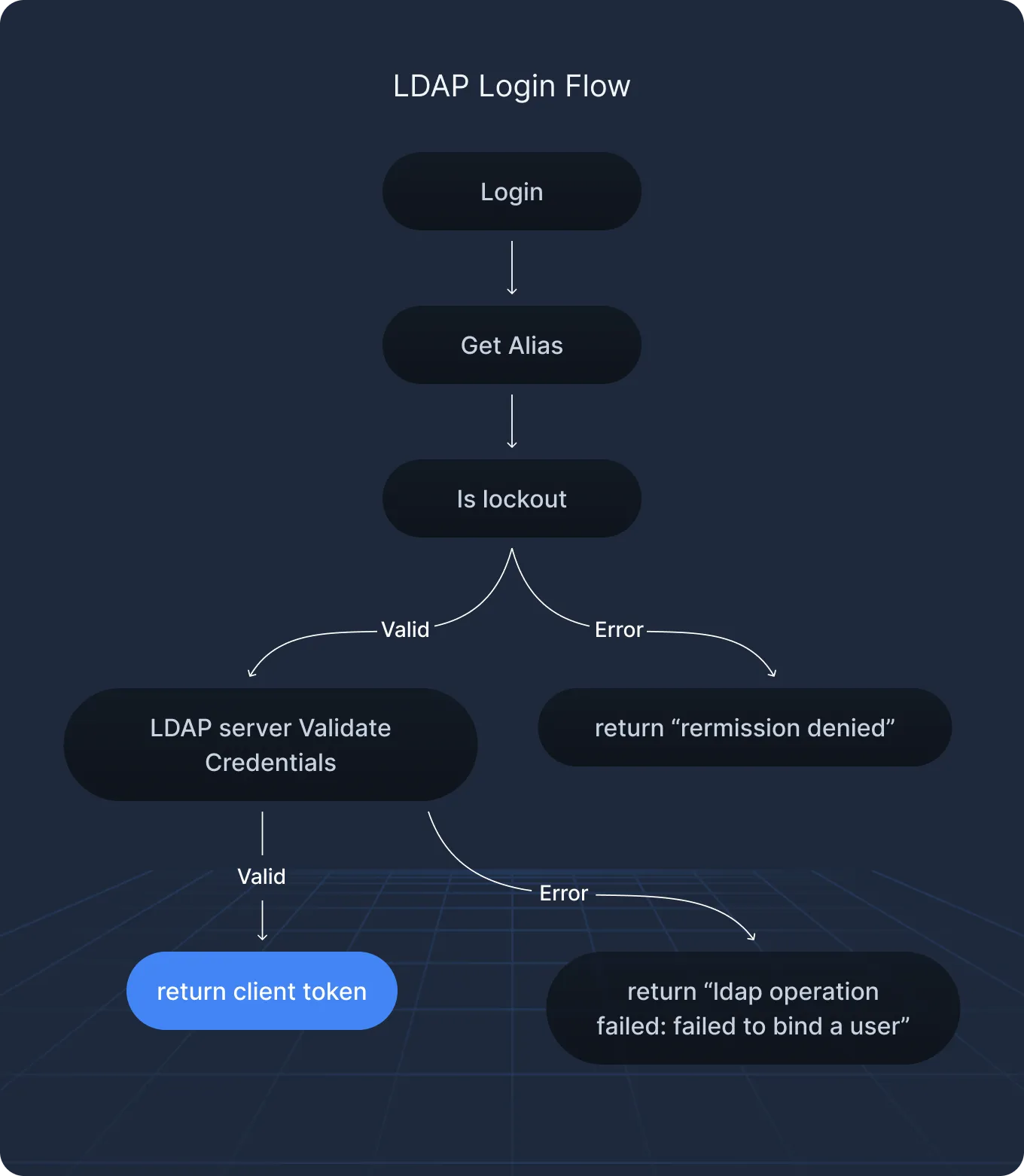
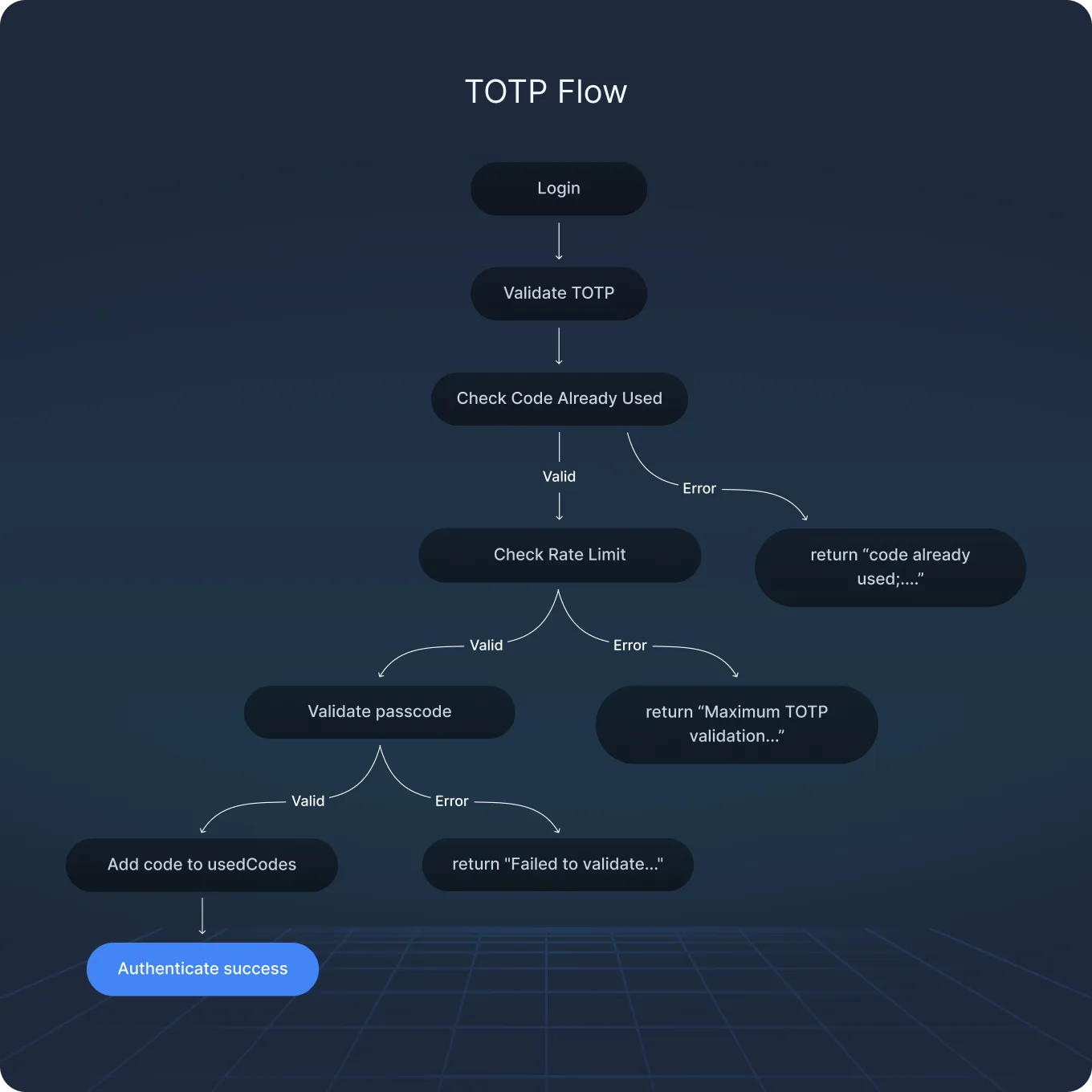
- Authentication Methods: Supports 14 backends, including userpass, LDAP, TLS certs, TOTP MFA — all of which were found vulnerable in specific ways.
- Policy Enforcement: Fine-grained, identity-based controls — undermined here by policy normalization bugs allowing privilege escalation.
- Plugin System: Extendable architecture — turned into an RCE delivery vehicle via audit log abuse.
The Big Caveats
The vulnerabilities fall into a few dangerous categories:
- Authentication Weaknesses: Username enumeration, lockout bypass via case/input normalization, MFA bypass via badly aligned identity mapping.
- MFA Logic Flaws: One-time-use bypass with space padding, rate-limit evasion through time skew and entity switching, passcode enumeration via verbose error messages.
- Identity Impersonation: Certificate-based auth in non-CA mode allows Common Name spoofing if private key is compromised.
- Privilege Escalation: Admin-to-root via bypassing hardcoded policy checks with whitespace/uppercase variants.
- Remote Code Execution: Plugin catalog manipulation via audit log abuse — first publicly reported RCE in Vault’s history.
When the vault’s trust model collapses, it’s not a leak — it’s a flood, and you’re already underwater.
Verdict
Avoid if you haven’t patched. Vault’s core promise is to safeguard secrets against all comers, and these flaws — existing for years — show it could be subverted without tripping alarms. HashiCorp has issued fixes in coordination with Cyata before public disclosure, so updated deployments may be safe. But given the age and subtlety of some of these bugs, treat unpatched Vault instances as high-risk assets. The real diagnosis? Vault’s security was living with silent chronic illnesses that just became acute. Patch immediately or prepare for critical system compromise.
And that, ladies and gentlemen, is entirely my opinion.
Source: Zero-day flaws in authentication, identity, authorization in HashiCorp Vault, https://cyata.ai/blog/cracking-the-vault-how-we-found-zero-day-flaws-in-authentication-identity-and-authorization-in-hashicorp-vault/